An introduction to cybercrime and cybersecurity as an investment theme
Cybercrime and cybersecurity are not new topics, but they have become more colloquial terms as the world adapted to facilitate “work from home” while nations grappled to get Covid under control. With the influx of people now working from private networks, which likely did not have the same level of security measures as that of the office they worked in prior to the pandemic, cyber criminals had a new pool of victims to target (and a lot of time on their hands as they too sat in quarantine). According to Deloitte, the proportion of sophisticated or unique cyber attacks increased to 35%, from 20%, during the pandemic.
As new technology is developed, it is also more vulnerable to attacks as the security infrastructure must be tried and tested to enhance its effectiveness. One such area, which Forbes noted as one which cybersecurity companies were focusing on, is the Internet of Things (IoT).
https://www.drishtiias.com/daily-news-analysis/securing-internet-of-things
The IoT is the connection of “things” and the internet. The “things” can be any item with a sensor that collects data on its environment and reports or acts on that information. The data is processed and transferred to improve efficiency, enhance innovation or boost customer service satisfaction. The IoT facilitates the transfer of large amounts of data between homes, workplaces and cities. An analysis quoted by Forbes in May 2022 noted that almost all of the data transferred by IoT devices were unencrypted (98%), and 57% of the devices contained personal data which was vulnerable to cyberattacks. Artificial Intelligence (AI) and Machine Learnings (ML) have been adopted to identify and control the risk posed by these new devices.
Although you may be thinking of your own safety while reading this, “Is it Siri or a cyber criminal listening?”, the threat spreads to geopolitics and large corporations who have integrated technology with their businesses (ie: almost all corporates). Geopolitical attacks may focus on critical supply chains and infrastructure. One of the main attacks to large corporates’ servers is that of a distributed denial-of-service (DDoS). This type of attack has caused even the most technologically advanced to fall to their knees (Google in 2017 and Amazon Web Services in 2020). DDoS attacks use a decentralised approach to attack a centralised target from various angles. Because the attack comes from many angles, the source is difficult to target and counteract. These attacks compromise the functionality of a company’s site and are sometimes used as a distraction while cyber criminals gain access to data. DDoS attacks have led to companies favouring a more decentralise design, a design blockchain is well known for.
Blockchain gained popularity through its link to Bitcoin, but it has a multitude of other uses. One area where it could be employed is cybersecurity. Due to its decentralised nature, gaining control of a complete piece of information requires that the various pieces be obtained from many sources – a costly exercise. If companies store their sensitive information through blockchain, they can be less susceptible to hacks as they are no longer a feasible target for hackers.
According to IBM, the average cost of a data breach in the US for 2022 is USD 9.4 million, up from USD 3.5 million in 2006. Cyber attacks can cost companies millions of dollars and they are enhancing their protection against such crimes. Increased awareness has led to more investment into cybersecurity and the infrastructure which supports it. It has been estimated in a survey by PwC that 69% of executives intended on increasing their spend on cybersecurity within the 2022 year.
Digitisation and the adoption of technology in the workplace has created new opportunities for cyber criminals, resulting in the need for enhanced protection for businesses of all sizes. This changing landscape, together with geopolitical tensions creates opportunity for cyber security focused companies.
The focus of cybersecurity companies can be categorised according to the three areas below:
- Endpoint security
- Security focused on prohibiting unauthorised access for devices, for example antivirus and antimalware providers
- Network security
- Security focused on protecting the internal network of an organisation
- Defence and aerospace
- Due to increased tension across geographies, many defence companies have enhanced focus on cybersecurity and its integration into their existing products
Most of the companies operating in this space offer a combination of the above solutions for their clients. For example, Check Point, an American-Israeli company, provides both endpoint and network security solutions. Check Point is highly regarded, with 1 in 4 Global Fortune 500 companies using their cloud security and a total client base of over 100,000 organisations. The company services both governments and corporates.
https://www.statista.com/statistics/595182/worldwide-security-as-a-service-market-size/
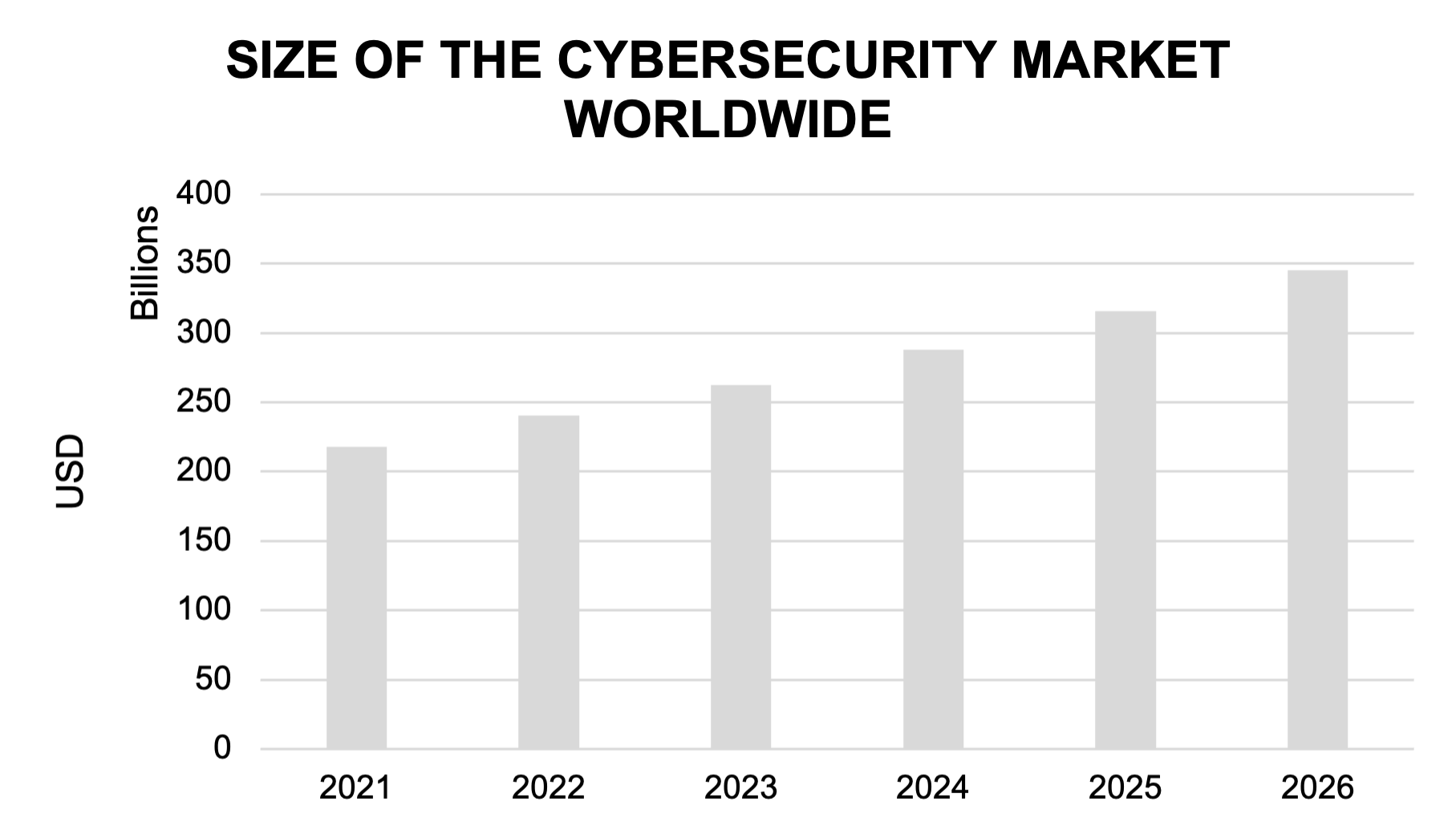
As cyber criminals continuously adapt to the challenges they are faced with when trying to access sensitive information, there will continue to be a need for innovation and development within cybersecurity. Organisations will not be able to afford to go uncovered and investments into their own security will continue. By 2026, the cybersecurity industry is expected to be around USD 345.4 billion. By including cybersecurity as a theme within portfolios, investors stand to benefit from this growth.
Currently, we have exposure to cybersecurity through companies we hold. One such company who was making the news earlier this year due to their involvement in this space is Alphabet (Google). Alphabet announced their acquisition of Mandiant, a cybersecurity platform, in March this year. Mandiant was previously known as FireEye, but rebranded after they sold their products business to McAffee in 2021. The acquisition cost was USD 5.4 billion (a small portion of the reported USD 140 billion cash Alphabet held on its balance sheet) and Alphabet attributed the purchase to the rise of cybercrime incidents and the increased cost associated with these crimes. Other companies we hold which have some exposure are: Amazon (Amazon Web Services); Cisco (Cisco Secure); and Apple (built in encryption features and protection). That does not mean we aren’t looking for more exposure; we at Pyxis are always on the lookout for valuable opportunities to incorporate into portfolios and this sector is one we definitely have on our radar.
Confused about all this tech jargon? Below is a breakdown of some of the more common terminology you may come across in warnings from service providers. As we head into the final leg of the year, keep aware of cyber criminals and be alert to any funnies you may encounter. If you are not sure of the authenticity of any correspondence – confirm the information telephonically with someone you trust at the sender. Don’t click on any links or forward any strange emails.
- PHISHING: An attacker impersonates someone else and entices their victim to click on a malicious link in order to steal their confidential information.
- MALWARE: Unwanted malicious software aimed at disrupting how your device works under normal conditions.
- RANSOMWARE: Interception of your device via malicious software which encrypts your data or locks you out of the system until a ransom is paid.
- SPYWARE: A type of malware which gathers your personal information and sends it on to advertisers and other external users.







